Statement:
The admin hides the flag, find it!
Author : K_lfa (BZHack / ESDAcademy)
I start by going to the URL provided and I see an MD5 hash in the GET value on the page parameter :
https://guessme.flag4all.sh//index.php?page=cfcd208495d565ef66e7dff9f98764da
The index.php returns the following value : NOPE, NOTHING HERE
I use hashcat to retrieve the value of the MD5 hash :
hashcat -a 0 -m 0 "cfcd208495d565ef66e7dff9f98764da" --wordlist rockyou.txt
Dictionary cache hit:
* Filename..: /home/sanlokii/pwn/wordlist/rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
cfcd208495d565ef66e7dff9f98764da:0
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: cfcd208495d565ef66e7dff9f98764da
Time.Started.....: Sun Oct 22 16:54:16 2023 (0 secs)
Time.Estimated...: Sun Oct 22 16:54:16 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/sanlokii/pwn/wordlist/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 7599.8 kH/s (0.25ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 2457600/14344384 (17.13%)
Rejected.........: 0/2457600 (0.00%)
Restore.Point....: 2441216/14344384 (17.02%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: 027276398 -> **miranda
Hardware.Mon.#1..: Temp: 69c Util: 8%
Started: Sun Oct 22 16:54:02 2023
Stopped: Sun Oct 22 16:54:18 2023
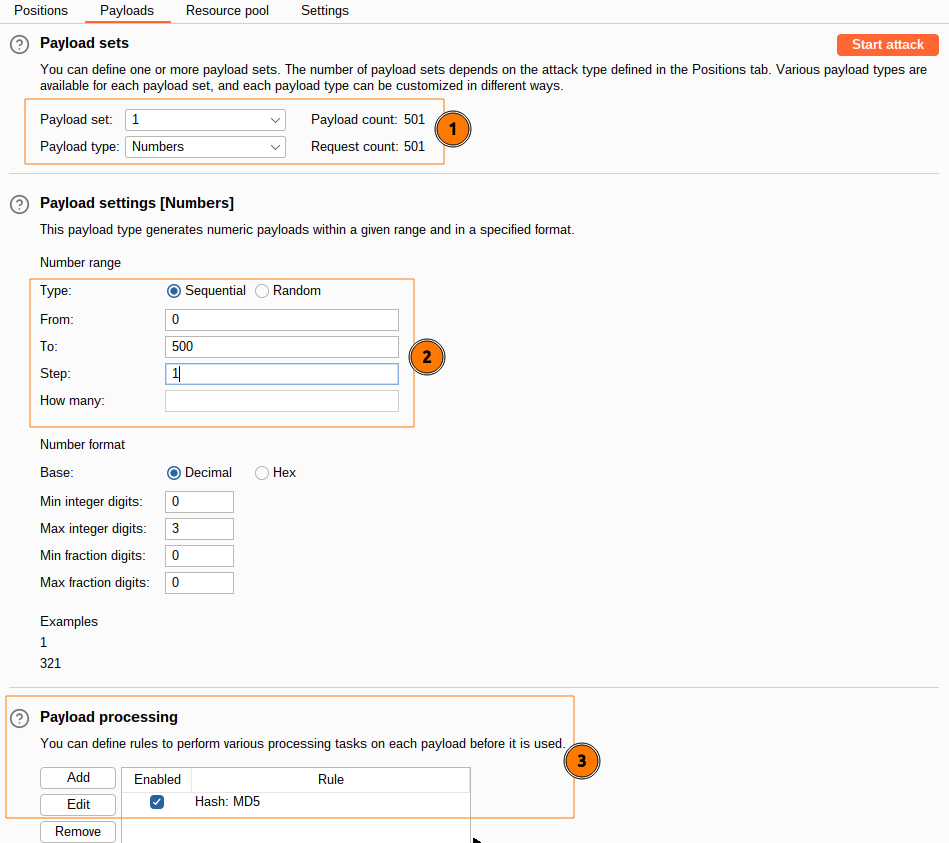
I now know that the MD5 hash value is 0 so I decide to fuzz the GET parameter :

In my payload, I specify the following parameters :
- List of numbers from 0 to 500, incremental by 1
- Hash numbers in MD5
After a few moments, the payload with a value of 350 hashed in MD5 returns the following result :
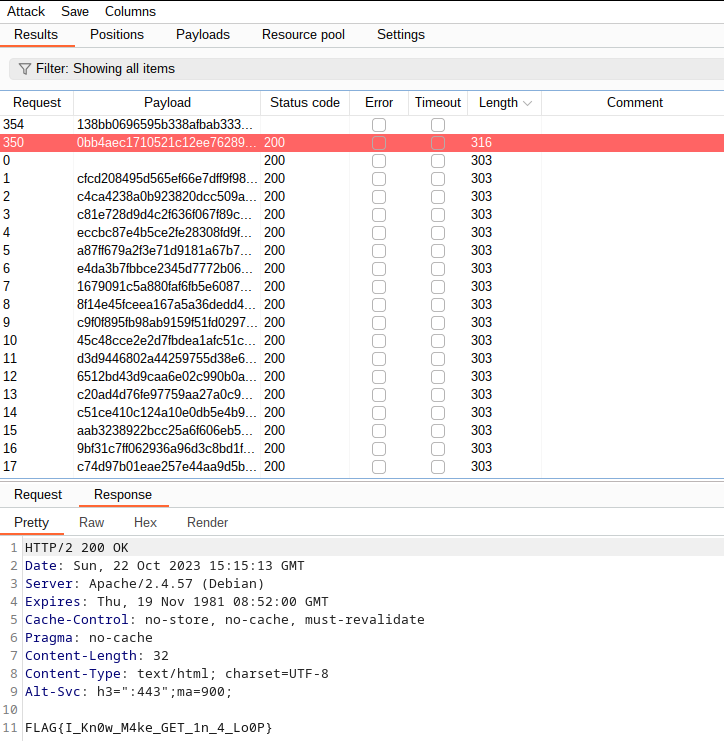
Flag: FLAG{I_Kn0w_M4ke_GET_1n_4_Lo0P}