Statement: if you see this you have to post in #memes thems the rules
docker run -tp 8000:8000 downunderctf/onions
I start by reading the history of the docker image:
sudo docker image history downunderctf/onions
IMAGE CREATED CREATED BY SIZE COMMENT
e4ad5b4d9379 3 days ago CMD ["/usr/local/bin/python" "-m" "http.serv… 0B buildkit.dockerfile.v0
<missing> 3 days ago EXPOSE map[8000/tcp:{}] 0B buildkit.dockerfile.v0
<missing> 3 days ago RUN /bin/sh -c rm memes/flag.jpg # buildkit 0B buildkit.dockerfile.v0
<missing> 3 days ago COPY . /app # buildkit 527kB buildkit.dockerfile.v0
<missing> 10 days ago WORKDIR /app 0B buildkit.dockerfile.v0
<missing> 2 weeks ago /bin/sh -c #(nop) CMD ["python3"] 0B
<missing> 2 weeks ago /bin/sh -c set -eux; wget -O get-pip.py "$… 10.9MB
<missing> 2 weeks ago /bin/sh -c #(nop) ENV PYTHON_GET_PIP_SHA256… 0B
<missing> 2 weeks ago /bin/sh -c #(nop) ENV PYTHON_GET_PIP_URL=ht… 0B
<missing> 2 weeks ago /bin/sh -c #(nop) ENV PYTHON_SETUPTOOLS_VER… 0B
<missing> 2 weeks ago /bin/sh -c #(nop) ENV PYTHON_PIP_VERSION=22… 0B
<missing> 2 weeks ago /bin/sh -c set -eux; for src in idle3 pydoc… 32B
<missing> 2 weeks ago /bin/sh -c set -eux; apk add --no-cache --… 30.5MB
<missing> 2 weeks ago /bin/sh -c #(nop) ENV PYTHON_VERSION=3.10.7 0B
<missing> 6 weeks ago /bin/sh -c #(nop) ENV GPG_KEY=A035C8C19219B… 0B
<missing> 6 weeks ago /bin/sh -c set -eux; apk add --no-cache c… 1.82MB
<missing> 6 weeks ago /bin/sh -c #(nop) ENV LANG=C.UTF-8 0B
<missing> 6 weeks ago /bin/sh -c #(nop) ENV PATH=/usr/local/bin:/… 0B
<missing> 6 weeks ago /bin/sh -c #(nop) CMD ["/bin/sh"] 0B
<missing> 6 weeks ago /bin/sh -c #(nop) ADD file:2a949686d9886ac7c… 5.54MB
I notice that the file containing probably the flag (flag.jpg) has been deleted during the last modifications.
So I decide to inspect the content of the image in search of information:
sudo docker inspect downunderctf/onions
One piece of information will catch my attention, the layers:
"RootFS": {
"Type": "layers",
"Layers": [
"sha256:994393dc58e7931862558d06e46aa2bb17487044f670f310dffe1d24e4d1eec7",
"sha256:bdd2dbc0f630af3f7c2cb6389503e7973143e950ae8d775e0905ca27ac43d6c1",
"sha256:765276be336a7e58719078ab0668c7fc2cc1da94bd07be942b3afa5f34890716",
"sha256:71aefba622a6cb157c4c969f3ecb5b258888c9163a50193263db5b35679b0784",
"sha256:804e16ced35b2b66dc7e569b56850f09edb4ecd9fe9fdb64882562d909335b74",
"sha256:95efea6a20579cecd96c550c1fb443a39f59ca12e4719c84951a8d38b6e02322",
"sha256:d22845d014e3f57356f7b944067bedaff9839534bb52e4ef93c8e40123022ec1",
"sha256:99d81c358faa406f7a0da8ab42896478d7da83230fa102d8fcf06b603ec71327"
]
}
After, I use the dive tool which allows to inspect the docker layers:
sudo dive downunderctf/onions
I see that the layer below with the ID 506946d44c8939efe882d5fd59797d22f2fe84adb7e2b7af066ca1563c11d464 contains the flag file:
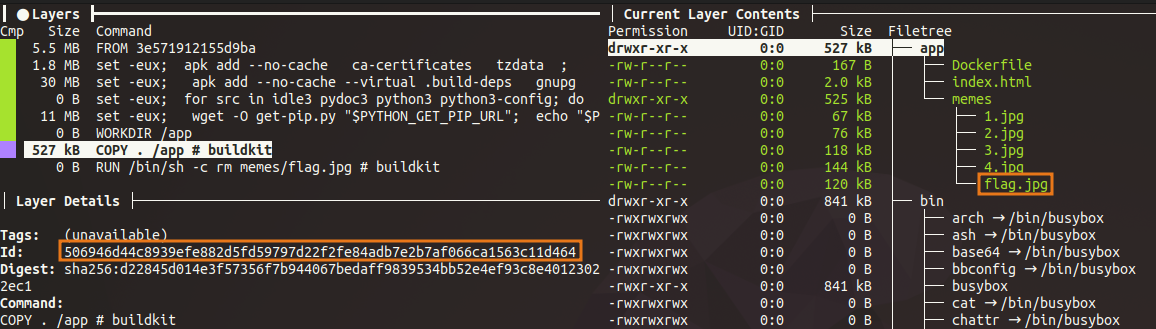
So I will save the image in a tarball:
sudo docker save -o flag.tar downunderctf/onions
Extract the content of the target layer and read the content of the file:
cd 506946d44c8939efe882d5fd59797d22f2fe84adb7e2b7af066ca1563c11d464 && sudo tar xvf layer.tar
Now, I just’ve to read the content of the file flag.jpg.
Flag: DUCTF{P33L_B4CK_TH3_L4Y3RS}